
As remote work continues to evolve, its impact on cloud web security becomes increasingly significant. By 2025, trends indicate a rise in cybersecurity threats, necessitating advanced solutions such as enhanced encryption and multi-factor authentication. Organizations must adapt their security protocols to protect sensitive data, ensuring a secure environment for remote employees while maintaining productivity and compliance with regulations.
As we move into 2025, the workplace landscape continues to evolve, with remote work becoming an integral part of the corporate environment. This shift has significant implications for cloud web security. Organizations are increasingly reliant on cloud services to facilitate remote operations, and understanding the trends and solutions in this domain is crucial for maintaining robust security measures.
The rise of **remote work** has led to a dramatic increase in the use of cloud-based applications. According to recent studies, over 75% of companies have shifted to cloud services to support their remote workforce. This trend underscores the need for heightened cloud web security. With employees accessing sensitive data from various locations and devices, the risk of cyber threats has escalated significantly.
Several trends are emerging as we approach 2025, shaping the future of **cloud web security** in a remote work environment:
1. Enhanced Zero Trust Architectures: The Zero Trust security model is gaining traction as organizations adopt a more cautious approach to data access. This model operates on the principle that no user or device should be trusted by default, regardless of their location. In 2025, we expect to see a more widespread implementation of **Zero Trust** frameworks, ensuring that every access request is rigorously verified.
2. Increased Use of AI and Machine Learning: Artificial intelligence (AI) and machine learning (ML) are becoming pivotal in identifying and mitigating security threats. These technologies can analyze patterns in user behavior and detect anomalies in real-time, providing organizations with a proactive approach to **cloud web security**. By 2025, we anticipate that AI-driven security solutions will be standard in cloud environments.
3. Focus on Endpoint Security: As remote work blurs the lines between personal and professional devices, securing endpoints has become critical. With employees using laptops, tablets, and smartphones to access corporate data, organizations must prioritize **endpoint security** solutions. In 2025, we expect to see a surge in the adoption of comprehensive endpoint protection strategies.
4. Growing Regulatory Compliance: As data breaches become more prevalent, regulatory bodies are tightening their grip on data protection laws. Companies will need to ensure compliance with regulations like the GDPR and CCPA. By 2025, organizations will have to invest significantly in compliance-focused **cloud web security** solutions to avoid hefty fines and reputational damage.
To navigate the evolving landscape of **cloud web security**, organizations must adopt effective solutions:
1. Implementing Multi-Factor Authentication (MFA): One of the most effective ways to enhance security is through **Multi-Factor Authentication**. By requiring users to provide multiple forms of verification, organizations can significantly reduce the risk of unauthorized access to sensitive data.
2. Regular Security Audits and Assessments: Conducting regular security audits helps organizations identify vulnerabilities within their **cloud web security** framework. By proactively addressing these weaknesses, companies can fortify their defenses against potential threats.
3. Training and Awareness Programs: Employee education is key to maintaining a secure remote work environment. Organizations should invest in regular training programs that focus on cybersecurity best practices, ensuring that employees are aware of the latest threats and how to mitigate them.
4. Cloud Security Posture Management (CSPM): CSPM tools help organizations manage their cloud security posture by continuously monitoring configurations and compliance. By adopting CSPM solutions, businesses can automate the identification of misconfigurations, reducing the risk of exploitation by cybercriminals.
Collaboration among teams is essential for effective **cloud web security**. IT, HR, and other departments must work together to establish security protocols that accommodate the needs of remote workers while safeguarding sensitive data. By fostering a culture of collaboration, organizations can create a comprehensive security strategy that addresses the unique challenges posed by remote work.
As we look ahead to 2025, the impact of **remote work** on **cloud web security** will continue to shape how organizations approach cybersecurity. By staying informed about emerging trends and implementing proactive solutions, businesses can protect their data, ensure compliance, and create a secure remote work environment. With the right strategies in place, organizations can thrive in this new era of work while safeguarding their most valuable assets.
How AI is Shaping Cloud Web Security Strategies in the USA for 2025
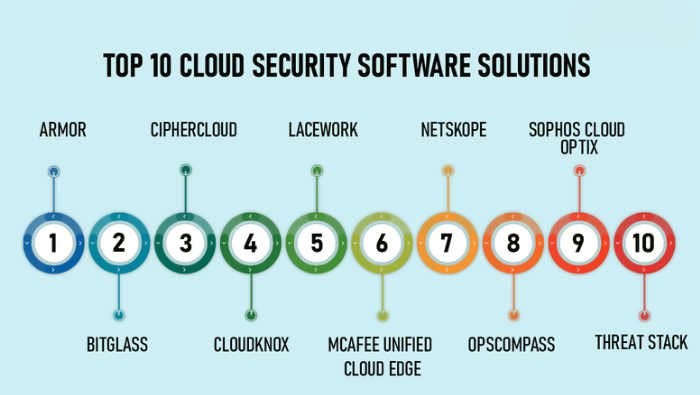
Top Cloud Web Security Solutions for Businesses in 2025: A Comprehensive Guide
Best 10 Reliable Cloud Backup Services: Secure Your Data

The Future of Cloud Web Security in the USA: Trends to Watch in 2025

Top Cloud Web Security Solutions in 2025: Protect Your Business in the Cloud

The Future of Remote Work: Employee Management Software Solutions for 2025
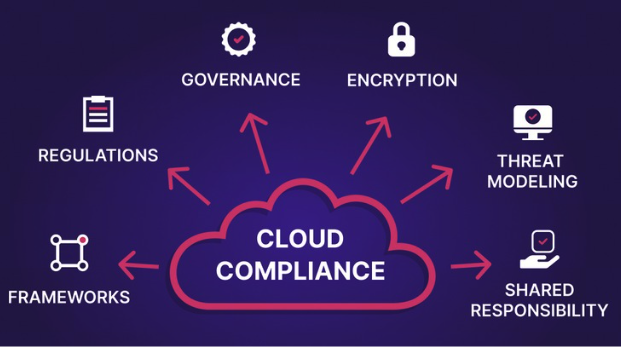
Navigating Compliance: Cloud Web Security Regulations in the USA by 2025
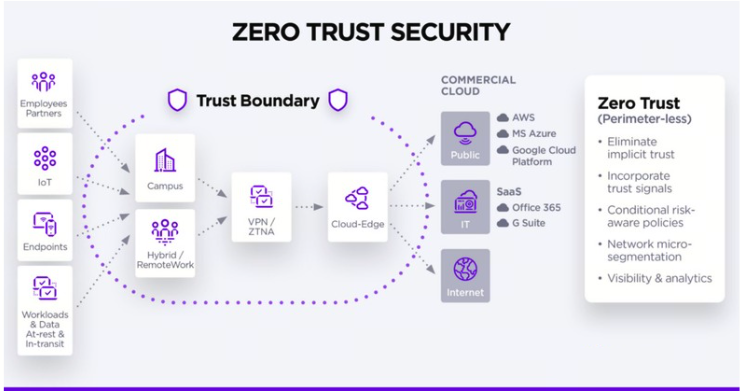
The Role of Zero Trust Architecture in Cloud Web Security: Insights for 2025